-
Products
-
Services
OT & IOT TestingBattle TwinReverse EngineeringReverse Engineering
- Pricing
- Team
- Blog
- Contact
- Join our community

Attack Surface Management (ASM) is your strategic defense mechanism against an evolving digital landscape. It casts a wide net over your organization’s attack surface, revealing hidden risks across all your internet-facing assets. Embracing advanced monitoring technologies, our ASM solution offers real-time insights into your digital ecosystem, equipping you to outsmart potential threats. From detecting vulnerabilities to enforcing rigorous security policies, we provide a comprehensive solution to ensure no facet of your security is left in the dark. Our ASM approach ensures your security posture remains robust, reducing exposure risk and continuously safeguarding your digital assets.

In the realm of cybersecurity, the prominence of cyber threats and the effectiveness of cyberattacks are intrinsically linked to the existence of open ports and the exposure of cyber assets. These vulnerabilities attract the attention of threat actors and cybercriminals, who exploit them to infiltrate networks. Our comprehensive solution acknowledges the paramount significance of maintaining constant vigilance over these vulnerable open ports. The exploitation of such ports can result in compromised services and the dissemination of malicious traffic via worms or malware. Through the deployment of cutting-edge technology, our solution empowers organizations to proactively monitor and mitigate these risks, ensuring robust protection and enhancing the security posture of their digital infrastructure.
In the field of cybersecurity, it is crucial to closely monitor critical internet infrastructure elements like domains, subdomains, and IP addresses. Our advanced solution empowers organizations to effectively oversee these assets, bolstering their security posture and reducing risks. By leveraging advanced technology and robust monitoring capabilities, our Digital Asset Monitoring module provides real-time visibility and proactive management of domains, subdomains, and IP infrastructure, fortifying the organization’s cybersecurity defenses.
In the constantly changing field of cybersecurity, it is crucial to prioritize the identification and resolution of vulnerabilities. Organizations face constant threats from adversaries seeking to exploit weaknesses in their digital infrastructure. Our cutting-edge vulnerability detection module provides comprehensive scanning and monitoring capabilities to identify and address potential vulnerabilities, ensuring robust protection against cyber threats.
Application Discover and the Technology Stack Discovery is a critical aspect of cybersecurity, focusing on protecting brand reputation and ensuring the integrity of web-based interactions. In today’s digital landscape, websites serve as the primary gateway for organizations to engage with their customers. It is essential to consider web applications as part of the overall cybersecurity strategy to mitigate potential risks and achieve a resilient digital infrastructure. Our advanced Web Application Monitoring module empowers organizations to proactively identify and address web security issues, safeguard brand reputation, and reduce the attack surface.
In the rapidly evolving digital landscape, safeguarding the reputation and integrity of a brand is of paramount importance. Our innovative Brand Monitoring module equips organizations with the tools and capabilities to proactively monitor and protect their brand identity in cyberspace. By leveraging advanced cyber technologies, our solution enables real-time detection and response to brand-related threats, ensuring brand resilience and maintaining customer trust.
In the dynamic landscape of cybersecurity, effective allocation of resources is paramount to protect critical assets. Our innovative Risk-based prioritization module utilizes advanced algorithms and cyber intelligence to prioritize assets based on their risk levels. This strategic approach enables organizations to optimize their security efforts, focusing resources on securing the most critical and vulnerable components of their digital infrastructure.
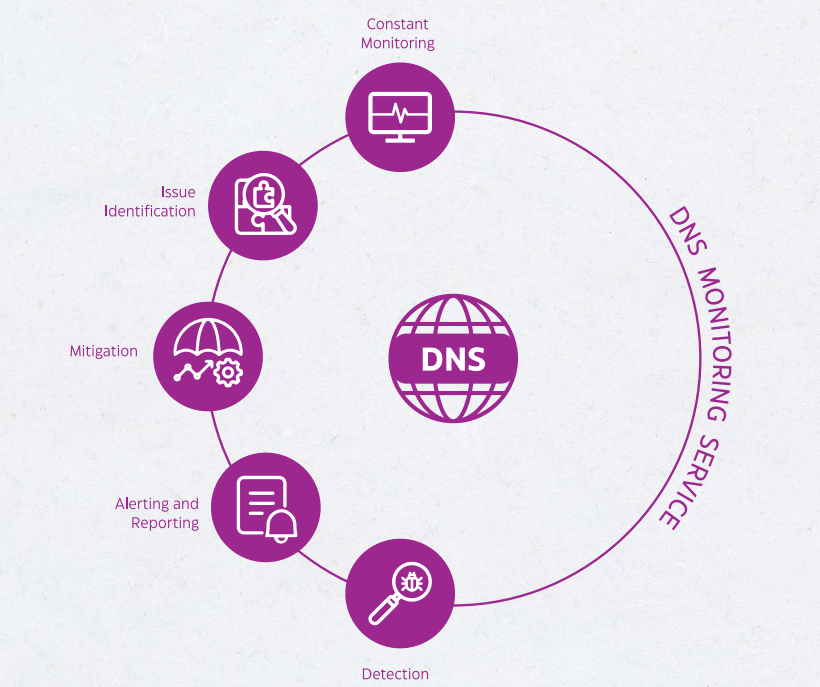
Organizations deploy multiple layers of perimeter security, such as next-generation firewalls, secure web gateways, sandboxing, intrusion prevention systems, anti-virus software, and endpoint detection and response (EDR) solutions, to counter various attack vectors. However, despite these measures, threat actors persist in exploiting vulnerabilities that exist beyond the perimeter. One notable example is DNS record manipulation (DNS hijacking), which has impacted numerous organizations, including telecoms, ISP providers, and infrastructure providers. Cytomate addresses this challenge by conducting frequent scans of SSL certificates associated with your domain and continuously monitoring DNS records. With real-time email alerts triggered by any changes in A, AAAA, CNAME, NS, or MX records.
SSL monitoring is the practice of actively monitoring and managing SSL/TLS certificates used for securing websites and online communication. It involves efficiently identifying potential cryptographic risks, conducting comprehensive surveillance of SSL/TLS certificates, continuously discovering, assessing, and monitoring the entire SSL certificate inventory, and receiving instant notifications when certificates are issued without consent. SSL monitoring is essential for maintaining the security and trustworthiness of online communications, protecting sensitive data, and ensuring the proper functioning of SSL/TLS certificates. It helps organizations proactively identify vulnerabilities, ensure compliance, prevent unauthorized certificate usage, and maintain a strong security posture.
Cytomate’s phishing campaign detection feature employs comprehensive domain analysis, covering a wide range of domain registrars, to identify malicious domains posing a threat to your brand and business network. It provides real-time alerts for any changes detected on suspicious domains. Additionally, Cytomate analyzes a vast database of domains to uncover lookalike domains that may be used for phishing attacks. The platform also offers proactive notifications, ensuring you stay informed about domain and SSL certificate expiration, thereby maintaining a secure digital presence.
Cytomate ASM provides a robust Dark and Surface Web Monitoring solution that equips organizations with the tools and insights necessary to effectively identify and mitigate threats spanning the surface, deep, and dark web. Leveraging cutting-edge reconnaissance capacities and meticulous threat analysis, the platform delivers actionable intelligence that empowers organizations to take proactive security measures. By monitoring the digital underworld, Cytomate ASM enables early detection of malicious activities and potential data breaches that may otherwise go unnoticed.
Cytomate utilizes risk scores to provide organizations with an objective measure of the potential threats and vulnerabilities associated with their digital infrastructure. The risk score calculation takes into consideration various factors, such as the criticality of the asset, its exposure level, and the severity of potential risks. By assigning risk scores to each asset, Cytomate enables organizations to prioritize their security efforts based on the level of risk they pose. This approach helps organizations focus on high-risk assets and allocate resources effectively to mitigate vulnerabilities, enhance their overall security posture, and proactively protect against potential threats.
The Cytomate ASM solution offers robust alerting capabilities, providing real-time notifications when security incidents, vulnerabilities, or suspicious activities are detected. This ensures that organizations are promptly informed, enabling them to take swift action and mitigate potential risks. Additionally, the Cytomate ASM system generates comprehensive reports that deliver detailed insights into security events, vulnerabilities, and risk management metrics. By combining effective alerting and detailed reporting. The Cytomate ASM solution empowers organizations to proactively respond to threats, enhance their overall security posture, and make data-driven decisions for effective risk management.