-
Products
-
Services
OT & IOT TestingBattle TwinReverse EngineeringReverse Engineering
- Pricing
- Team
- Blog
- Contact
- Join our community

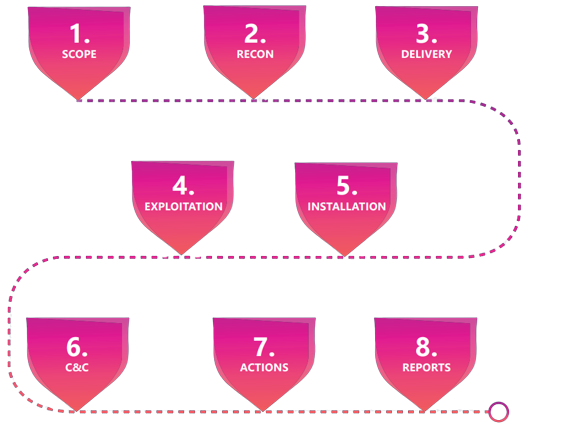
Cytomate’s Red Teaming Services are designed to provide organizations with a comprehensive evaluation of their security posture by emulating a real-world attack scenario. The service helps businesses identify vulnerabilities in their systems, processes, and policies that could be exploited by attackers. The team of expert security professionals at Cytomate uses a combination of automated and manual techniques to identify weaknesses in the security infrastructure and emulate attacks on the organization’s systems. The results of the red teaming exercise help organizations identify areas that need improvement and implement the necessary changes to strengthen their security posture.
A red team assessment is a goal-oriented adversarial activity that necessitates a complete view of an organization from the adversary's perspective. This evaluation approach is intended to satisfy the demands of complex organizations that manage a diverse range of sensitive assets via technical, physical, or process-based means.
The purpose of conducting a red teaming assessment is to demonstrate how real-world attackers can combine seemingly unrelated exploits to achieve their goal. It's an efficient technique to demonstrate that even the most advanced firewalls are worthless if an attacker can walk out of the data centre with an unencrypted hard disc. Rather than depending on a single network appliance to safeguard sensitive data, it is preferable to employ a defence in depth strategy and continually enhance your people, processes, and technology.
Our red team tests replicate realistic virtual and physical security attacks to identify security defects that would go undiscovered by hostile actors and present an accurate picture of the risks and vulnerabilities posing a threat to your technology, people, and physical assets. The Red Team is responsible for network security, social engineering, application-level security, and physical security.
Different Qatar based reputed firms have used our Red Team's services. Cytomate has enhanced the security posture of these organizations by finding different types of vulnerabilities and threats. We first exploit these vulnerabilities and then report them to the specific organization. We are providing some possible mitigations and fixes against these vulnerabilities for better reporting. By identifying and managing risks, threat agents' capacity to steal data, drain revenue, or inflict other harm on their firm is dramatically reduced.