-
Products
-
Services
OT & IOT TestingBattle TwinReverse EngineeringReverse Engineering
- Pricing
- Team
- Blog
- Contact
- Join our community

Sarab, the cutting-edge cyber deception system, exemplifies the harmonious fusion of cutting-edge hardware technologies with innovative cyber strategies. But it’s more than just about technological prowess; it’s about reimagining the very philosophy of cybersecurity. Historically, deception has been an artform practiced by generals and strategists for thousands of years. From the battlefield strategies of ancient civilizations to modern chess games, deception has always been about misleading the opponent, making them see a reality that benefits the deceiver.
Drawing upon this time-honored wisdom, Sarab transforms the cyber defense arena. Instead of merely acting as a passive shield against cyber threats, Sarab takes a proactive stance. It doesn’t wait in the shadows; it invites potential attackers into a controlled environment. This arena is meticulously designed, not to harm but to study these cyber adversaries. Every move they make and every strategy they employ is observed, analyzed, and learned from.
Cyber deception represents a transformative approach in the realm of cybersecurity, moving away from the more conventional reactive measures we’ve seen in the past. Traditional systems often remain dormant, operating on a defensive footing, poised, and waiting for a potential cyberattack. In contrast, cyber deception takes a more audacious stance, actively seeking to confront and confound cyber threats. Sarab stands as a prime exemplar of this bolder strategy. It does more than just shield digital assets; it employs a web of deception, strategically redirecting, bamboozling, and ultimately neutralizing cyber adversaries.
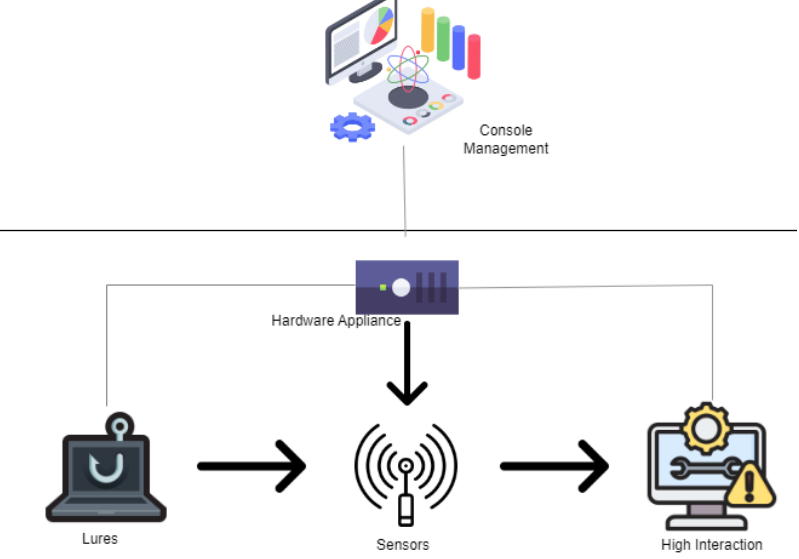
At the heart of Sarab’s innovative deception methodology are the customized high and low interaction honeypots. The high interaction honeypots are intricately designed to mirror genuine systems, captivating attackers and drawing them into a deeper engagement. This immersive environment allows for a comprehensive gathering of intelligence, revealing the attackers’ methods, tools, and intentions. On the other hand, low interaction honeypots serve a more direct purpose. They emulate particular services and ports, acting as initial tripwires to identify and reroute potential threats. By harnessing both these honeypots, Sarab casts a wide and effective net, capturing a diverse range of threats from the surface-level scans to intricate, multi-layered cyber intrusions. Furthermore, Sarab is adeptly crafted for adaptability and quick deployment. It’s architected to seamlessly integrate and expand across multiple subnets, making it a versatile fit for both startups and multinational corporations. The cherry on top is its centralized console management system, a testament to its user-centric design. This feature guarantees that, despite its broad operational expanse, realtime-monitoring and managing Sarab’s deception ecosystem remains streamlined andintuitive
A distinguishing factor that elevates Sarab above other cyber deception tools is its exceptional ability to deploy bespoke honeypots. Unlike the one-size-fits-all solutions commonly found in the market, Sarab’s honeypots are meticulously crafted to match an organization’s distinct digital identity. This means that every honeypot mirrors the precise configurations, services, and applications that are characteristic of the host organization. By doing so, it achieves an unparalleled level of authenticity, making it virtually impossible for attackers to discern they’re interacting with a decoy. This brilliant subterfuge not only confounds cyber adversaries but also yields a wealth of valuable intelligence, as they unknowingly reveal their tactics, techniques, and procedures in what they believe to be a genuine environment.
The power of Sarab is greatly amplified through its tight-knit integration with Security Information and Event Management (SIEM) systems. Each and every engagement with the honeypots, from the most inconspicuous probe to the most intricate attack pattern, is carefully logged. This wealth of information is then channeled directly into SIEM platforms, providing security professionals with an in-depth, real-time perspective of the evolving threat environment. But Sarab’s synergy doesn’t end there. With its integration to STIX (Structured Threat Information eXpression), Sarab guarantees that the threat data is presented in a standardized format. This ensures a seamless exchange of threat intelligence across various platforms and tools, enabling a more unified and effective response to cyber threats.
In the world of cybersecurity, the Breach and Attack Simulation (BAS) stands as a cutting-edge strategy. Sarab’s integration with Breach+ transforms its defense mechanisms into something extraordinary. When Sarab ensnares malware within its deceptive landscape, the action doesn’t stop at merely containing it. Leveraging the power of Breach+, the malware’s attack sequence is recreated and played out in a controlled simulation. This proactive step allows security professionals to gauge whether the malware had the potential to evade the current defense barriers. Such simulations offer a rare glimpse into potential weak spots, highlighting areas that might require bolstering or immediate remediation.
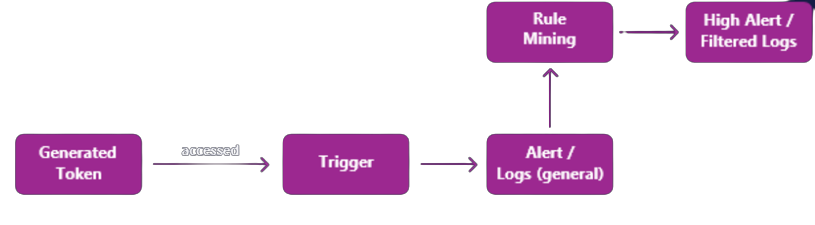
In the context of internal deception, a Cybermine refers to a virtual decoy or a honey token that is placed in the network to attract attackers. These decoys can take different forms, such as fake user accounts, network shares, or even false data elements. Cybermines are designed to look and feel like real assets to an attacker, which lures them into interacting with the decoy. Once an attacker interacts with the mine, the system captures their behavior and analyzes it to gain insights into their tactics and techniques. Rule mining is one of the techniques used in internal deception to extract rules from MITRE TTPs and database logs. These rules are used to customize and fine-tune the system’s behavior to better match an organization’s specific needs and requirements. Rule mining can include conditional or scenario-based rules, reference-based rules, and attribute dependency-based rules. By mining these rules, organizations can gain a better understanding of potential attack scenarios and take proactive measures to prevent attacks from happening.