The rising threat of cyberattacks on industrial control systems has become a critical concern for organizations worldwide. To address this growing challenge, we introduce "Battle Twin", an innovative virtualized environment-based solution designed for conducting attacks using breach and attack simulations tailored specifically for OT networks, isolated from production environment.
Battle Twin rigorously tests the effectiveness of security controls such as Defender for IoT, Dragos, and other competitors in detecting a wide range of attacks and threat behaviors. By providing a realistic and risk-free environment, Battle Twin empowers security experts to evaluate and improve the detection capabilities of their security measures. This ultimately enhances the resilience of operational technology systems against cyber threats.
Battle Twin simulates some of the most prominent communication protocols used in real OT environments, like Modbus, DNP3, Profinet, BACnet, OPC-UA. This means you get a genuine testing ground for simulating breaches and attacks. Since it mirrors the actual protocols used in OT, Battle Twin creates a true-to-life virtual replica of your network, making your testing experience as realistic as possible.
Battle Twin features an extensive library of attack types for IT and OT networks, covering OT devices, protocols, and network attacks. Each attack is mapped to MITRE ICS Matrix TTPs. Battle Twin also emulates industrial malware like BlackEnergy and Triton. Cytomate's Reverse Engineers extract and recreate malware TTPs for simulation. These controlled simulations, monitored by your security solution, identify vulnerabilities without harming real OT equipment or networks.
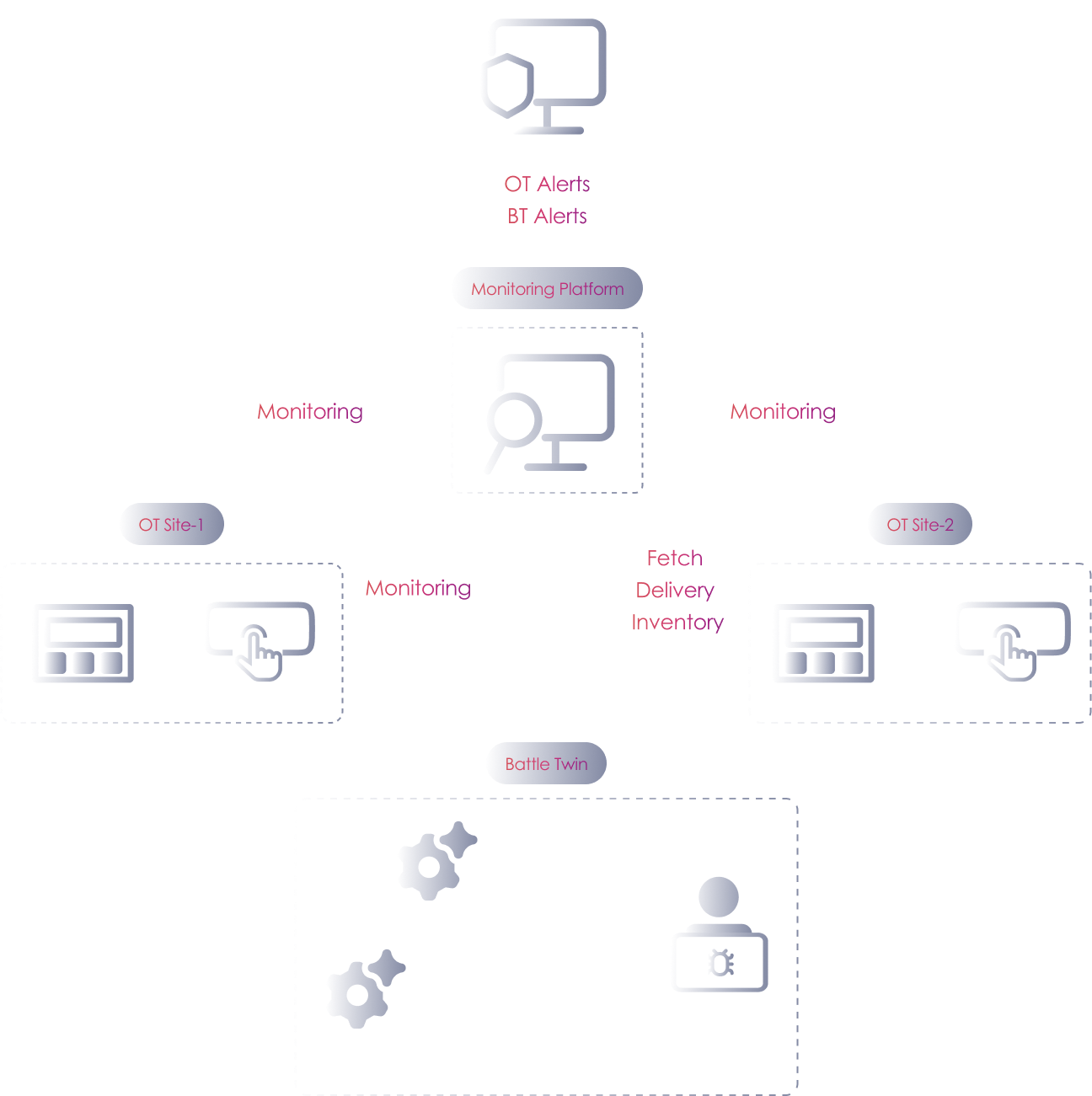
Battle Twin provides insights into the effectiveness of your security measures against potential threats. It creates a virtual replica of your OT environment, integrating with security monitoring sensors to capture and analyse all internal traffic. After establishing a baseline of normal activity, Battle Twin initiates the attacks on the simulated environment to test detection and response. This process identifies undetected attacks and addresses security gaps.
By meticulously analysing the response and detection capabilities of security controls for each individual attack, Battle Twin produces comprehensive reports that identify any threats that went undetected. These reports offer a detailed breakdown of which attacks evaded detection and the specific weaknesses in the security controls that allowed this to happen.
Battle Twin can easily be integrated with ICS/OT security monitoring sensors, regardless of their vendor i.e. Defender for IoT, Nozomi Networks Guardian/Vantage, Claroty CTD among others. It test and validates the effectiveness of existing security controls, including IDS and IPS, by triggering real-time alerts.
Provides detailed explanation and detection of attacks, enhancing the overall security measures.