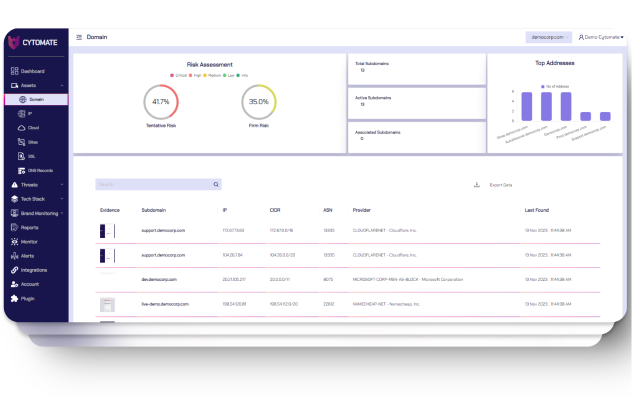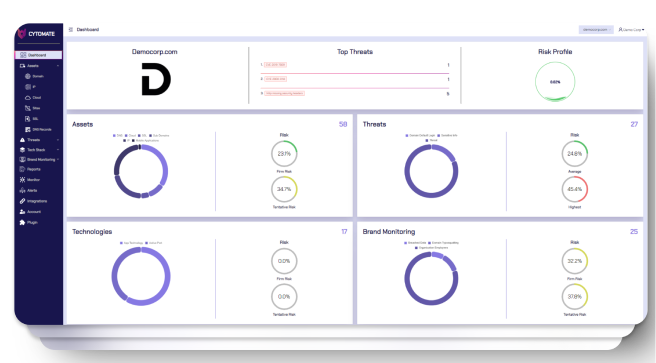
Cytomate's Racid an External Attack Surface Management SaaS based solution is designed to provide organizations with comprehensive visibility and control over digital assets. It aims to identify, monitor, and mitigate risks associated with the attack surface to enhance external security posture. Embracing advanced monitoring technologies, our ASM solution offers real-time insights into your digital ecosystem, equipping you to outsmart potential threats. From detecting vulnerabilities to enforcing rigorous security policies, we provide a comprehensive solution to ensure no facet of your security is left in the dark. Our ASM approach ensures your security posture remains robust, reducing exposure risk and continuously safeguarding your digital assets. Choose ASM for a vigilant, fortified, and proactive approach to application security.
Discover known and unknown external assets (subdomains, IPs, DNS records, whois records, SSL certificates, cloud assets, ports, tech stack, web and mobile applications)
Real-time monitoring of all discovered assets. Alert if anything is changed for example whois record changed, web application is altered.
Real-time Monitor Surface, Deep and Dark web and telegram channels for an organization. Discover and monitor phihsing campaigns with impersonated domains and OSINT and provide takedowns. Social media and VIP monitoring coming soon and provide takedown.
Provide breach data of employees and customers from stealerlogs and breachforums. Discover and monitor pastebins and related content sharing platforms and provide takedowns. Discover Rouge mobile applications and provide takedowns.
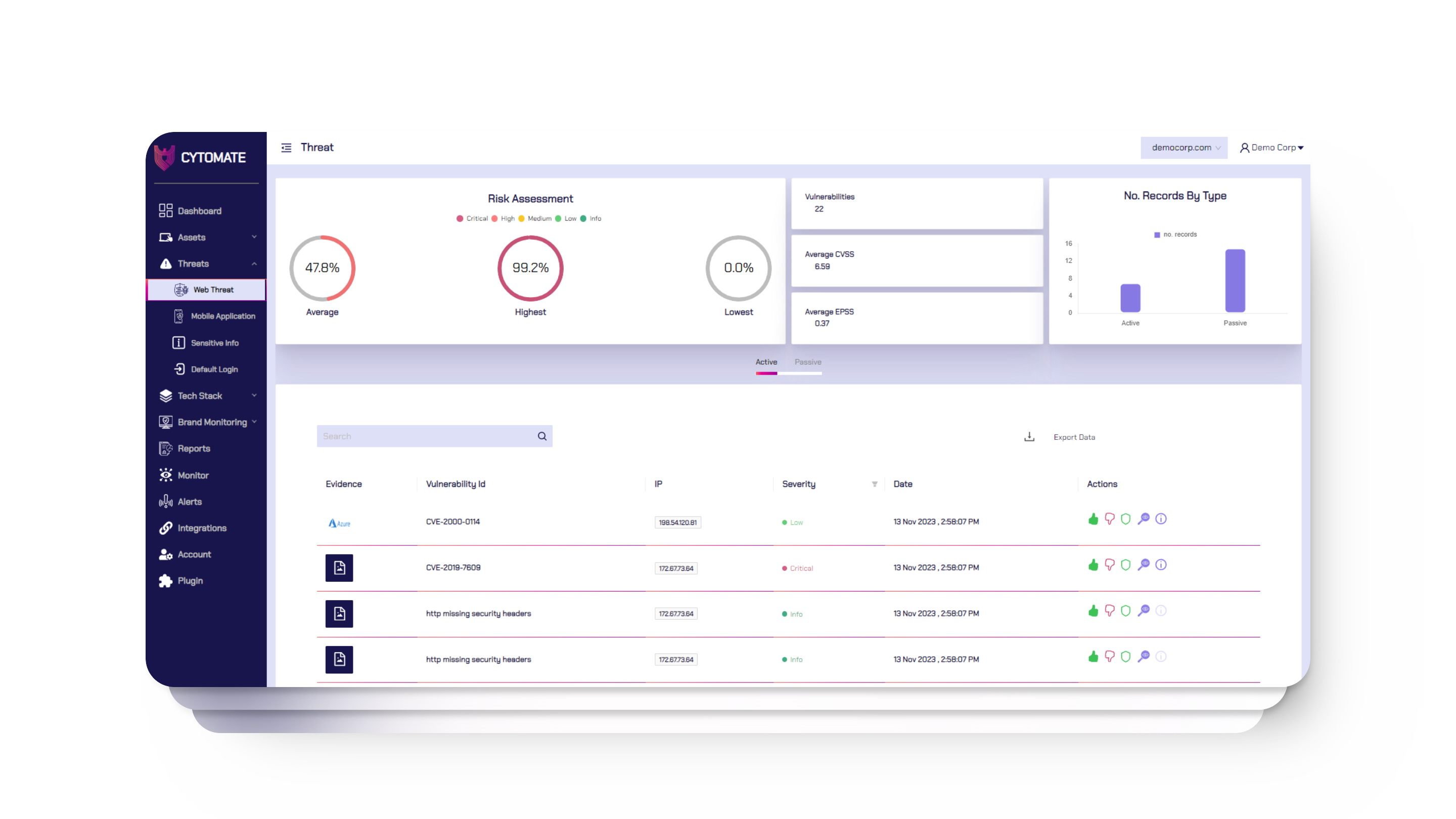
Active threat mapping on web applications and servers based on OWASP, to proactively discover CVEs, and Misconfigurations.
Passive threat mapping on web application and servers based on identified tech stack.
Static mobile application testing.
Discover leaked secrets across external facing attack surface in JS files, code repositories or servers.
Cloud threat mapping with integration to discover security misconfigurations.
Provides excel, json and pdf reports.
Provides alert on user interface and email, additionally to integrated solutions like JIRA or Slack.
Cloud providers
Slack
Jira and Teams (coming soon)
Combines proactive risk management, continuous threat monitoring, and vulnerability management to ensure a robust defense against potential threats.
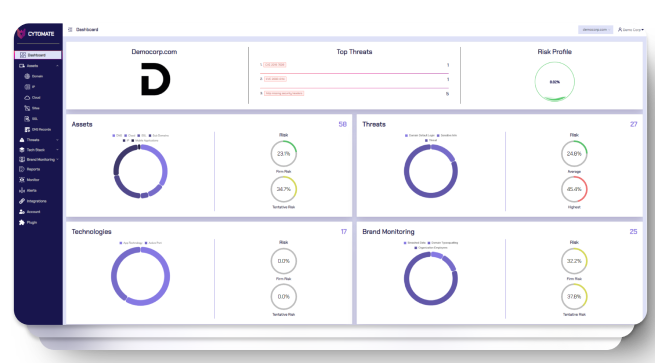
Optimizes resource use by automating security tasks and centralizing asset management, leading to better allocation of time and effort.
Centralizes asset management and continuously monitors threats, providing comprehensive visibility and control over the organization's security posture.