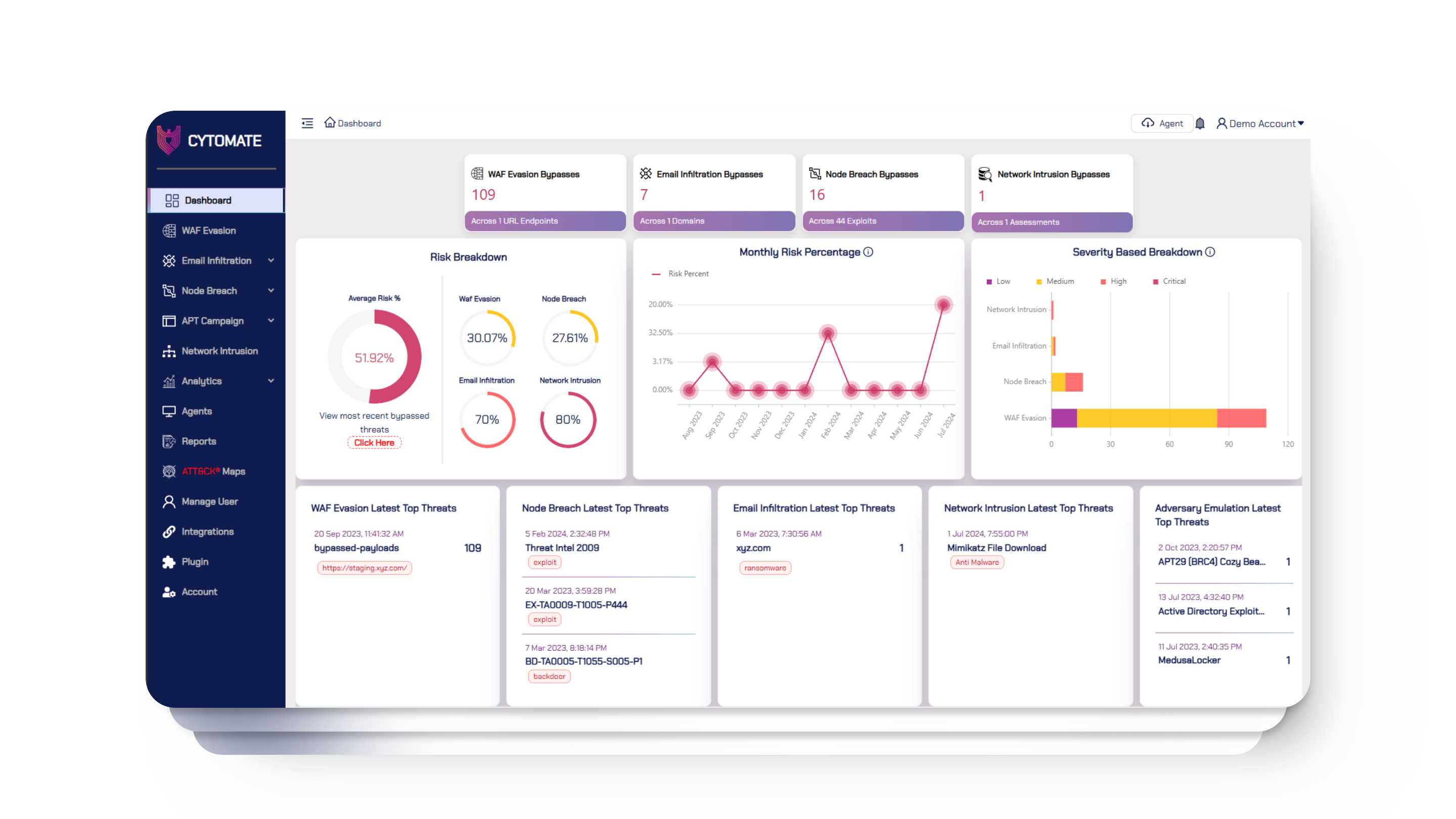
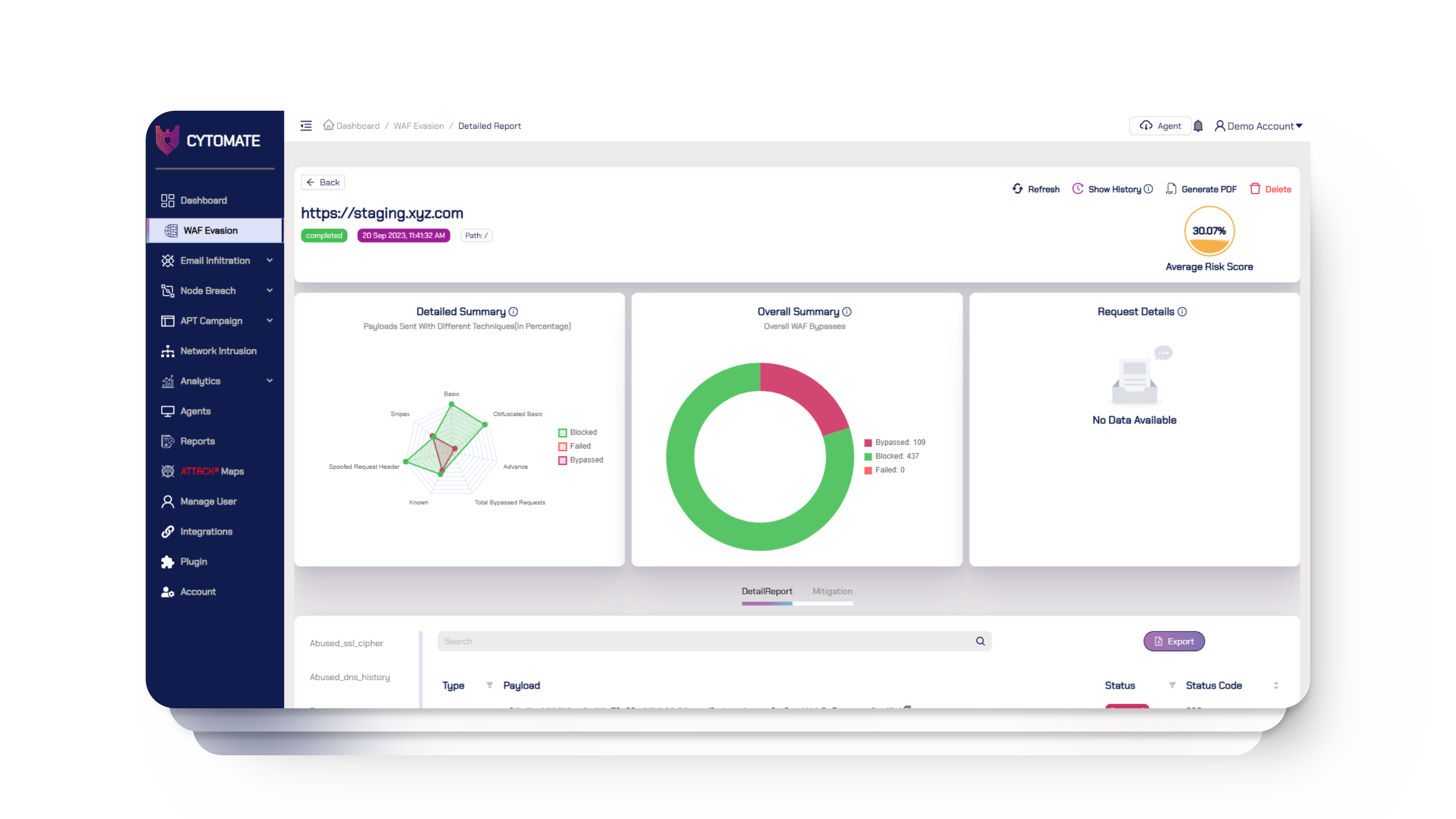
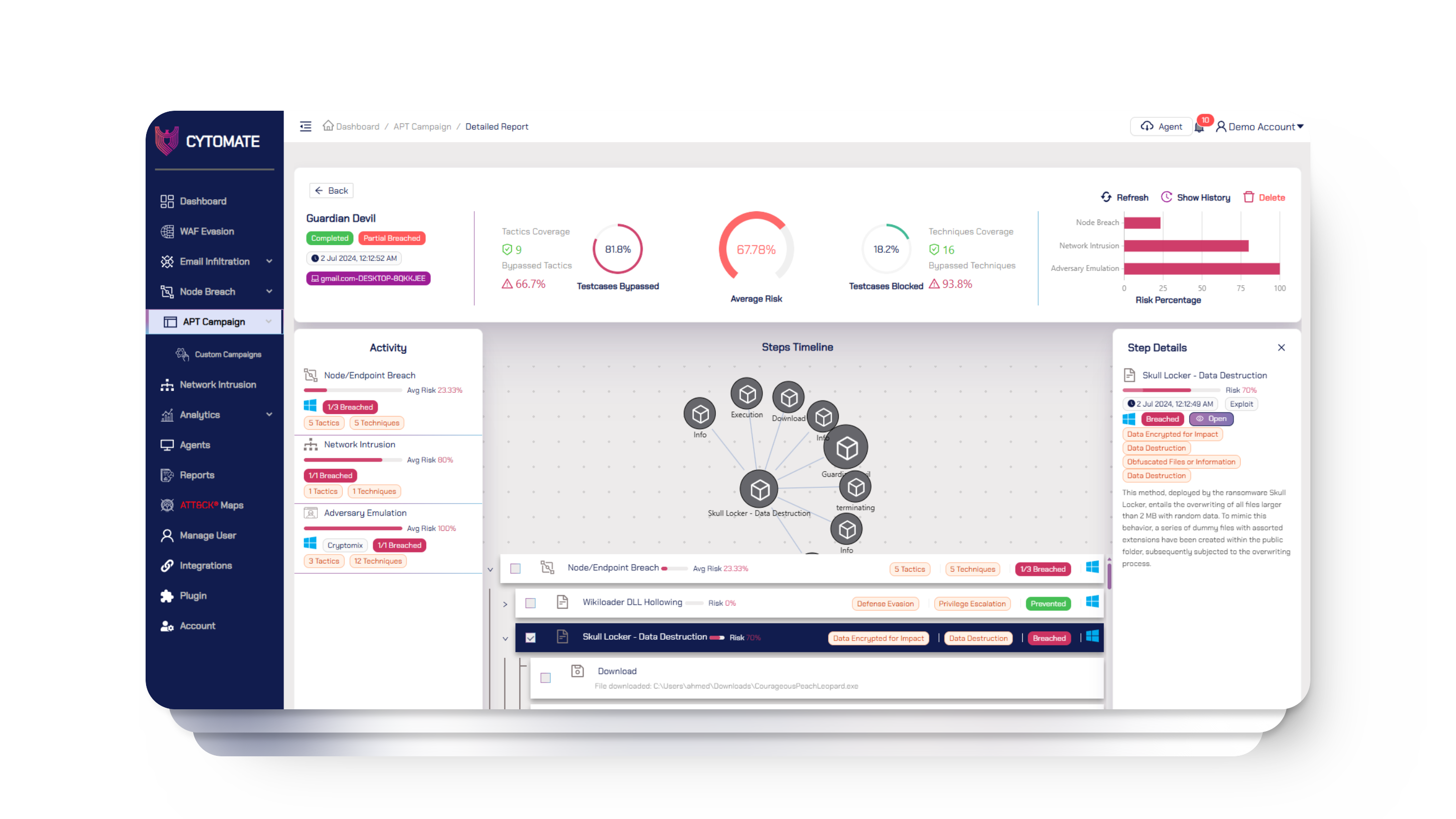
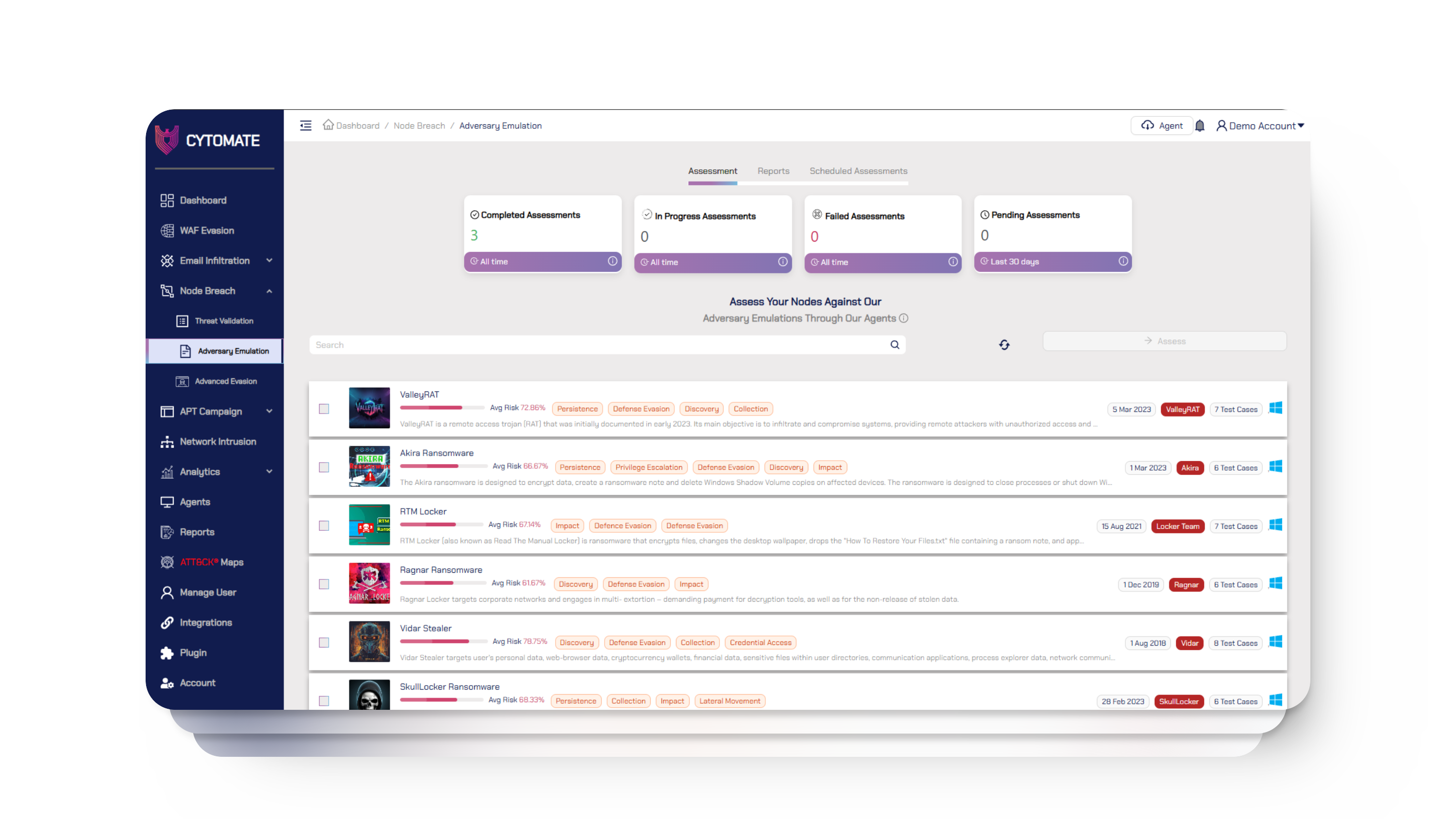
Breach+
Breach+ is awarded the Common Criteria Certification by the National Cyber Security Agency where this is certification is an ISO/IEC 15408 and recognized by +31 countries worldwide. This reflects our commitment to ISO/IEC 15408 and recognized by +31 countries worldwide. This reflects our commitment to delivering secure and reliable solutions, meeting the highest international standards for information security. The product is vetted on the national level bya: